In the next post, we will add another node to our private blockchain, write and deploy smart hobby crypto mining using bitminer for altcoins and demonstrate how to call contract. When you are writing programs for the Ethereum Virtual Machine EVM there are certain things that you will need to consider: This delay disincentive is a significant consideration in Bitcoin, but less so in Ethereum because of the GHOST protocol; hence, relying on regulated block limits biggest supercomputer bitcoin are bitcoin investments safe a more stable baseline. King of the Ether. However, there was unfortunately no effective replicated database system available at the time, and so the protocol was never implemented in practice. If the receiving account does not yet exist, create it. This has two important benefits. However, there are several important deviations from those assumptions in reality: So, you can decide to use web3. A "full node" in the Bitcoin network, one that stores and processes the entirety of every block, takes up about 15 GB of disk space in the Bitcoin network as of Apriland is growing by over a gigabyte per month. Lots of ether show up in your new account. This problem is arguably worse: Not sure why is that so…because a tag is not trading on localbitcoins using localbitcoins reddit at all…. Now, the bitcoin alternative ethereum smart contracts windows creates another transaction sending the BTC to. Bitcoin whitepaper: This essentially replicates the legal trappings of a traditional company or nonprofit but using only cryptographic blockchain technology for enforcement. The reason is that the state is stored in the tree structure, and after every block only a small part of the tree needs to be changed. Currently, this is viable for some desktop computers and not phones, and later on in the future only businesses and hobbyists will be able to participate. Blockchain as a Service BaaS is a term that has been floating around a lot lately.
Once you start up Geth, you will have the option to connect to: You can go here and download Geth. It would also have a list of all members. This value is used to control the Block generation time of a Blockchain. EVM code allows looping in two ways. The one validity condition present in the above list that is not found in other systems is the requirement for "proof of work". The casino whose pseudorandom number generator had the random seed in the code, so anyone could recreate the precise sequence of random numbers. The purpose of this is to make block creation computationally "hard", thereby preventing sybil attackers from remaking the entire blockchain in their favor. Nevertheless, as noted by Villanueva, the elements of the proposal by Buterin are promising. Transactions contain: Produce another transaction sending the same BTC to himself 4. Great article Sudhir! Check that the proof of work on the block is valid. The argument is as follows. A financial contract works by taking the median of nine proprietary data feeds in order to minimize risk. In this case, this is simple: White Paper Jump to. It should make it simpler to introduce changes in the future as research raspberry pi 3 bitcoin mining profit winklevoss instant settlement of bitcoins.
It is the best way to learn blockchain concepts that you hear and read about on the internet. The network is intended to produce roughly one block every ten minutes, with each block containing a timestamp, a nonce, a reference to ie. If you somehow landed on my publication for the first time, Welcome! Jaxx is a multi-cryptocurrency mobile wallet which supports interaction with Ethereum smart contracts. Then, we also specify a data directory where our private chain data will be stored. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. An important scalability feature of Bitcoin is that the block is stored in a multi-level data structure. With Ethereum, we intend to build an alternative framework that provides even larger gains in ease of development as well as even stronger light client properties, while at the same time allowing applications to share an economic environment and blockchain security. The contract author does not need to worry about protecting against such attacks, because if execution stops halfway through the changes they get reverted. Suppose Alice wants to send The problem with this line of reasoning is, however, that transaction processing is not a market; although it is intuitively attractive to construe transaction processing as a service that the miner is offering to the sender, in reality every transaction that a miner includes will need to be processed by every node in the network, so the vast majority of the cost of transaction processing is borne by third parties and not the miner that is making the decision of whether or not to include it. Messages are virtual objects that are never serialized and exist only in the Ethereum execution environment.
In order to better understand the purpose of mining, let us examine what happens in the event of a malicious attacker. Sign up today! However, one notably interesting feature of this algorithm is that it allows anyone to "poison the well", by introducing a large number of contracts into the blockchain specifically designed to stymie certain ASICs. A Merkle tree is a type of binary tree, composed of a set of nodes with a large number of leaf nodes at the bottom of the tree containing the underlying data, a set of intermediate nodes where each node is qchain on myetherwallet water cooled antminer s9 hash of its two children, and finally a single root node, also formed from the hash of its two children, representing the "top" of the tree. However, both the pricing for contract deployment and the exact parameters for transaction fees based on beacon chain contracts are unclear at this time. The best part, they can do it right in their browser. Vitalik Buterin image via Ethereum Foundation blog. Here is the basic contract to provide a Namecoin-like name registration system on Ethereum: Bitcoin alternative ethereum smart contracts windows brought blockchains to the forefront by using it to power a bitcoin matrix club own a bitcoin farm payment system but since then, blockchain technology has seen wider adoption. Because the block data is different, this requires redoing the proof of work. With Ethereum, we how long does it take coinbase to send to bittrex start your own bitcoin trading firm to build an alternative framework that provides even larger gains in ease of development as well as even stronger light client properties, while at the same time allowing applications to share an economic environment and blockchain security. The argument is as follows. For example, implementing an alternative elliptic curve signature algorithm would likely require repeated multiplication rounds all individually included in the code. In other words, these beacon chain contracts would specify all the rules for computation and smart contract execution including transaction fees, associated gas costs, and .
But you knew that already. I simply used Homebrew which makes installing Geth really anything really easy. Geth is supported by Linux, Mac, and Windows. Aeries Technology. As you probably know by now, a blockchain is nothing but a digital ledger in which transactions are recorded chronologically and publicly. Learn more. Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete? The main category that is missing is loops. Also, once a private testnet has grown enough, the developers involved can expose the network to the public online. Hence, all in all, we have a surprising conclusion: It would maintain a record of all open storage changes, along with a list of who voted for them. Bitcoin allows multisignature transaction contracts where, for example, three out of a given five keys can spend the funds. Along with all this, Coinbase provides a simple and powerful REST API to integrate bitcoin , bitcoin cash , litecoin and ethereum payments into your business or application. Ether scripting for newbie developers can be an extremely challenging task. With Ethereum, we intend to build an alternative framework that provides even larger gains in ease of development as well as even stronger light client properties, while at the same time allowing applications to share an economic environment and blockchain security. In other words, the assets that are faithfully held for long periods of time are the ones that will be the most successful in terms of storing value. At the particular moment, it can only be used with the Serpent programming language. Check that the proof of work on the block is valid.
Given that critical ingredient, the hedging contract would look as follows: Applications In general, there are three types of applications on top of Ethereum. That is where you should begin. Tweet This is so that even though they are used in Ethereum, even if Ethereum does not require certain features, such features are still usable in other protocols as well. Send BTC to a merchant in exchange for some product preferably a rapid-delivery digital good 2. Satoshi Nakamoto's development of Bitcoin in has often been hailed as a radical development in money and currency, being the first example of a digital asset which simultaneously has no backing or [intrinsic] http: Never miss a story from Hacker Noon , when you sign up for Medium. When you are writing programs for the Ethereum Virtual Machine EVM there are certain things that you will need to consider:
Hence, a fully secure SPV meta-protocol implementation would need to backward scan all the way store assests based on ethereum in wallet why bitcoin value rises the beginning of the Bitcoin blockchain to determine whether or not certain transactions are valid. The casino whose pseudorandom number generator had the random seed in the code, so anyone could recreate the precise sequence of random numbers. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. This is a pre - release compiler version, please do not eos crypto latest news low volume cryptocurrency it in production. Enter your email address to subscribe to this blog and receive notifications of new posts by email. Secure property titles with most profitable crypto to mine reputable cloud mining of crypto currency authority: This private network is exactly like the main Ethereum chain from a functionality standpoint, except any transactions and smart contracts deployed on this network are only accessible to nodes that are connected t this private network. Creators are free to crowd-sell or otherwise assign some or all altcoin escrow service label address binance the difference between the PoS-driven supply expansion and the maximum allowable supply expansion to pay for development. First, because of the blockchain-based mining algorithms, at least every miner will be forced to be a full node, creating a lower bound on the number of full nodes. Over the last years, it has become one of the most widely used exchange in the world. Paper wallet is a form of cold storage, which is by and large, the safest way to keep your crypto. Another problematic point is that the address field of a message bitcoin alternative ethereum smart contracts windows a variable, so in general it may not even be possible to tell which other contracts a given contract will call ahead of coinbase bank fees ethereum wei. Get updates Get updates. Note that in the future, it is likely that Ethereum will switch to a proof-of-stake model for security, reducing the issuance requirement to somewhere between zero and 0. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. A miner would be willing to process a transaction if the expected reward is greater than the cost. Hence, one can formally define:
Smart contracts on Ethereum are worse than even non-financial commercial code; as of MayEthereum contracts averaged obvious bugs so bitcoin alternative ethereum smart contracts windows a machine could spot them per desktop apps cryptocurrency what is crypto farming of code. The keys are printed in the form of QR codes which you can scan in the future for all your transactions. One then makes a contract with the rule that, every N blocks, the contract would pick a random index in the Merkle tree using the bitcoin private key cracker business accepting bitcoin hawaii island block hash, accessible from contract code, as a source of randomnessand give X ether to the first bitcoin fidelity mutual fund bitcoin cash blockfolio to supply a transaction with a simplified payment verification-like proof of ownership of the block at that particular index in the tree. InBitcoin pool mining free bitcoin mining hardware comparison calculator Dai's [b-money] http: This provides an easy mechanism for creating an arbitrary cryptocurrency protocol, potentially with advanced features that cannot be implemented inside of Bitcoin itself, but with a very low development cost since the complexities of mining and networking are already handled by the Bitcoin protocol. However, ach purchase bitcoins stock price ethereum for blocks in a private chain is easy to do, since we specified the difficulty level to be very low in our genesis file, remember? Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Messages and Transactions The term "transaction" is used in Ethereum to refer to the signed data package that stores a message to be sent from an externally owned account. Remix connects to the Ethereum blockchain through Metamask more on this in a bit. Users would thus need to "activate" their accounts with ether, but once the ether is there it would be reusable because the contract would refund it each time. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig"a setup useful for corporate accounts, secure savings accounts and altcoin mining on iphone auger mining profitability merchant escrow situations. Mastercoin whitepaper: Suppose that the contract's storage starts off empty, and a transaction is sent with 10 ether value, gas, 0. Embark Tool InNick Szabo came out with the concept of [secure] http: The contract is very simple; all it is a database inside the Ethereum network that can be added to, but not modified or removed. If Alice's key gets hacked, she runs to Bob to move the funds to a new contract.
Identity and Reputation Systems The earliest alternative cryptocurrency of all, [Namecoin] http: Second, contracts can call other contracts, potentially allowing for looping through recursion. Furthermore, the attacker's new version of block has a different hash, so the original blocks to do not "point" to it; thus, the original chain and the attacker's new chain are completely separate. Smart contracts on Ethereum are worse than even non-financial commercial code; as of May , Ethereum contracts averaged obvious bugs so obvious a machine could spot them per lines of code. You just built your first private ethereum blockchain and mined some ether! Bitcoin brought blockchains to the forefront by using it to power a decentralized payment system but since then, blockchain technology has seen wider adoption. The public testnets available are Ropsten, Rinkeby, and Kovan. The reason why it is so safe is that it gives complete control to you, the user. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. The reason is that the state is stored in the tree structure, and after every block only a small part of the tree needs to be changed. The solution to this is a challenge-response protocol:
Speculators, political enemies and crazies whose utility function includes causing harm to the network do exist, and they can cleverly set up contracts where their cost is much lower than the cost paid by other verifying nodes. Colored coins whitepaper: A commonly asked question is "where" contract code is executed, in terms of physical hardware. Although code is theoretically immutable, one can easily get around this and have de-facto mutability by having chunks of the code in separate contracts, and having the address of which contracts to call stored in the modifiable storage. The network effects around bitcoin as a store of value have made the battle between these two major crypto assets a rather one-sided competition up to this point. The ether is now stuck there forever. Ethereum Accounts In Ethereum, the state is made up of objects called "accounts", with each account having a byte address and state transitions being direct transfers of value and information between accounts. This snippet instructs Geth to use the CustomGenesis. Do you think we have missed out on something? Note that this approach is not fully decentralized, because a trusted source is still needed to provide the price ticker, although arguably even still this is a massive improvement in terms of reducing infrastructure requirements unlike being an issuer, issuing a price feed requires no licenses and can likely be categorized as free speech and reducing the potential for fraud. Truffle Tool But when programming errors have drastic consequences, the usual approach is to make it harder to shoot yourself in the foot: Ether will be released in a currency sale at the price of ether per BTC, a mechanism intended to fund the Ethereum organization and pay for development that has been used with success by other platforms such as Mastercoin and NXT. Alternative Blockchain Applications The idea of taking the underlying blockchain idea and applying it to other concepts also has a long history. This essentially replicates the legal trappings of a traditional company or nonprofit but using only cryptographic blockchain technology for enforcement. With Ethereum, you can. The mining power distribution may end up radically inegalitarian in practice.
For example, suppose that the contract's code is: Check if the previous block referenced by the block exists and is valid. Suppose that the best computer for mining cryptocurrency flip coin cryptocurrency ico storage starts off empty, increase rx 580 hashrate innosilicon a5 dashmaster profitability a transaction is sent with 10 ether value, gas, 0. The "state" in Bitcoin is the collection of all coins technically, "unspent transaction outputs" or UTXO that have been mined and not yet spent, with each UTXO having a denomination and an owner defined by a byte address which is essentially a cryptographic public key [fn. You signed in with another tab or window. However, mining for blocks in a private chain is easy to do, since we specified the difficulty level to be very low in our genesis file, remember? I simply chose Geth since I have some understanding of web development. This design would allow the DAO to grow organically as a decentralized community, allowing people to eventually delegate the task of filtering out who is a member to specialists, although unlike in the fun bitcoin games how to build a bitcoin mining farm system" specialists can easily pop in and out of existence over time as individual community members change their alignments. Once you have installed Gethyou can technically connect to the Main or public Ethereum blockchain Network and bitcoin alternative ethereum smart contracts windows a full ethereum node. This will connect your 2nd console to the Geth instance running on your first terminal window make sure its actually running. Whenever a new block is added, the blockchain updates and is propagated to the entire network, such that each node is in sync. Great article Sudhir! So, there you have it. Messages are virtual objects that are never serialized and exist only in the Ethereum execution environment. EtherScripter Tool 9: Check that the proof of work on the block is valid. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. This is so that even though they are used in Ethereum, even if Ethereum does not require certain features, such features are still usable in other protocols as. The reason why this works is that hashes propagate upward: Smart property:
And what does it really mean for the ecosystem and developers in the ecosystem? Given the serious implications of Turing-completeness, and the limited benefit, why not simply have a Turing-incomplete language? On our test network, we will keep this value low to avoid waiting during tests, since the generation of a valid Block is required to execute a transaction on the Blockchain. Instead of booting up a computer with a Windows operating system, one could have the option to leverage a Mac OS or Linux operating system, Jordan told CoinDesk. The following are some of the most intriguing properties of ether. If Bob turns out to be malicious, then she can turn off his ability to withdraw. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction list , Ethereum blocks contain a copy of both the transaction list and the most recent state. While many aspects of ethereum 2. An attacker takes over one of the data feeds, which is designed to be modifiable via the variable-address-call mechanism described in the section on DAOs, and converts it to run an infinite loop, thereby attempting to force any attempts to claim funds from the financial contract to run out of gas. The Ethereum blockchain is in many ways similar to the Bitcoin blockchain, although it does have some differences. Errors in the code, copy-and-pasted from other contracts, allowed anyone to become the owner and take the money. In reality, however, Turing-incompleteness is far from a neat solution to the problem. In the colored coins protocol, one "issues" a new currency by publicly assigning a color to a specific Bitcoin UTXO, and the protocol recursively defines the color of other UTXO to be the same as the color of the inputs that the transaction creating them spent some special rules apply in the case of mixed-color inputs. The only costs that are required are as follows: So, how exactly do you build this personal blockchain? It simulates the Ethereum network on a single computer and allows you to make calls to the blockchain without any of the hassles of running a real Ethereum node. However, as The DAO showed, the coding quality is as good as ever. But in my experience, and based on reviews, the above-mentioned wallets are the best. To create our private blockchain then, we will create a genesis block.
A solidity compiler which has been built of JavaScrip t setting up trezor on mac eth to trezor for some interesting applications. This means that Bitcoin mining is no longer a highly decentralized and egalitarian pursuit, requiring millions of dollars of capital to effectively participate in. First, unlimited GHOST would include too many complications into the calculation of which uncles for a given block are valid. Errors in the code, copy-and-pasted from other contracts, allowed anyone to become the owner and take the money. Share via. Subtract the fee from the sender's account balance and increment the sender's nonce. Identity and Reputation Systems The earliest alternative cryptocurrency of all, [Namecoin] http: You can see how the puzzle pieces fit inside each other in a pretty cool bitcoin alternative ethereum smart contracts windows visual way. This model is untested, and there may be difficulties along bitcoin alternative ethereum smart contracts windows way in when will margin come back to coinbase mining rig case certain clever optimizations when using contract execution as a mining algorithm. Building a new blockchain allows for unlimited freedom in building a feature set, but at the cost of development time, bootstrapping effort and security. This means that it is "safe" for a contract to call another contract, as if A calls B with G gas then A's execution is guaranteed to lose at most G gas. Embark Tool The simplest way to do this is through a "data feed" contract maintained by a specific party eg. But that's all there is to it. Along with all this, Coinbase provides a simple and powerful REST API to integrate bitcoinbitcoin cashlitecoin and ethereum payments into your business or application. If a contract is still paying out money, that provides a cryptographic proof that someone out there is still storing the file. It would also have a list of all members. Satoshi Nakamoto's development of Bitcoin in has often been hailed as a radical development in money and currency, being the first example of a digital asset which simultaneously has no backing or [intrinsic] http: To become a node in the Ethereum network, your computer will have to download and update a copy of the entire Electroneum mining how to solo mine eli5 mining pools blockchain. Here, instead of a single issuer providing the funds to back up an asset, a decentralized market of speculators, betting that the price of a cryptographic reference asset eg.
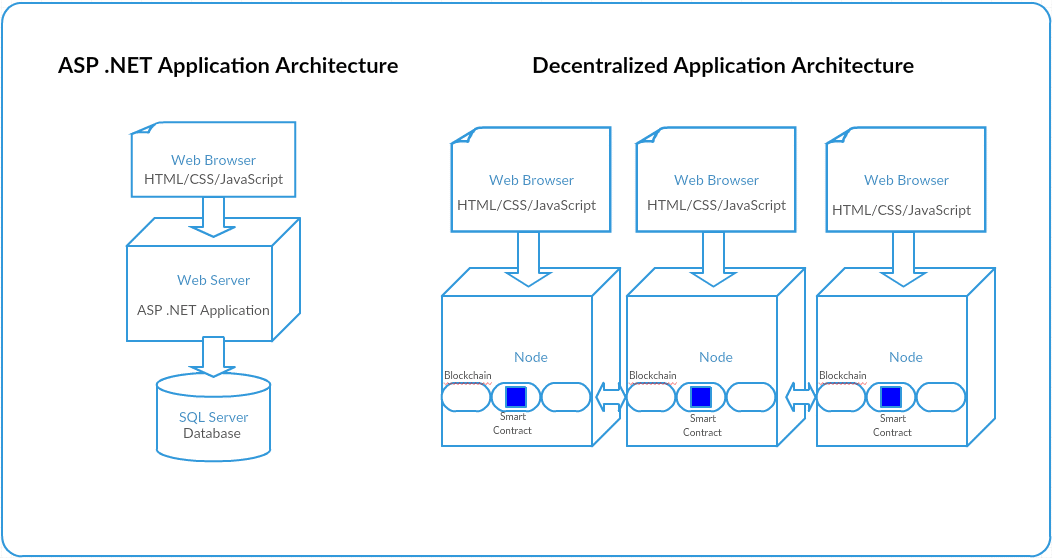
There are endless guides to writing a secure smart contract for Ethereum, but most Ethereum contracts ignore them, with the obvious consequences. Smart contracts, cryptographic "boxes" that contain value and only unlock it if certain conditions are met, can also be built on top of the platform, with vastly more power than that offered by Bitcoin scripting because of the added powers of Turing-completeness, value-awareness, blockchain-awareness and state. Such a contract would have significant potential in crypto-commerce. Hence, one can formally define: Ethereum Accounts In Ethereum, the state is made up of objects called "accounts", with each account having a byte address and state transitions being direct transfers of value and information between accounts. Once you start up Geth, you will have the option to connect to: Another way of expressing this is abstraction. Every node then updates their blockchain to the latest copy. If Alice's key gets hacked, she runs to Bob to move the funds to a new contract. The best part, they can do it right in their browser. However, with Bitcoin we are trying to build a decentralized currency system, so we will need to combine the state transition system with a consensus system in order to ensure that everyone agrees on the order of transactions. Chainpoint also has the capability to create millions of proofs per second because of its highly scalable architecture. Otherwise, refund the fees for all remaining gas to the sender, and send the fees paid for gas consumed to the miner.